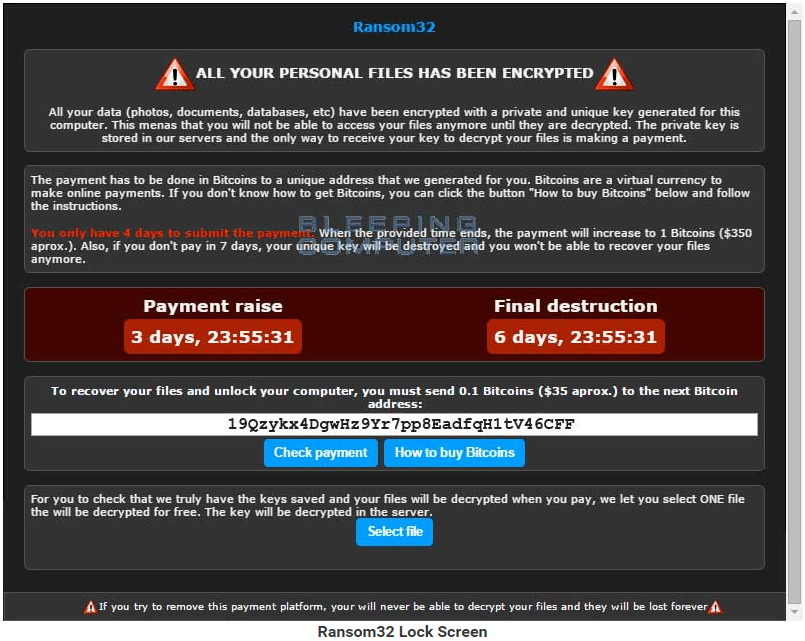
The Year 2015 saw cyber criminals implement new strategies to extort money, many taking their ransoms in bitcoin. The one that got everybody’s attention as the year came to a close was Ransom32 – a JavaScript-based ransomware which freezes the files in a user’s computer until a ransom is paid in bitcoin.
The revelation was first made on BleepingComputer.com by an infected user who complained that he could not access the data on his computer, including pictures, documents, and mp3.
Bleeping Computer editor Lawrence Abrams told BBC.com that the infection “was designed for those that lacked the technological skill to create their own brands of malware.”
Security expert Graham Cluley also told BBC:
“By turning their ransomware into a sellable service, the criminals behind Ransom32 are providing an opportunity for other hackers to easily launch attacks that will encrypt users’ documents, including personal photographs, movies and more.“
Security expert Fabian Wosar of Emsisoft and security researcher xXToffeeXx analyzed this Ransomware as a Service or RaaS, and have brought to light some important facts about the infection.
Key Points About Ransom32
- It is located on an underground TOR network, and can be downloaded when a bitcoin address is submitted.
- After a user submits the bitcoin address, he is presented with an administration panel, where he can configure the amount of bitcoin in ransom, and get access to data such as the number of people who already paid the ransom.
- The program is the first virus written in HTML, CSS and JavaScript languages.
- The malware developers demand a 25% cut of any ransom collected the user downloading the virus and send the rest to the bitcoin wallet address supplied.
How Does it Work?
After finishing the configuration of Ransom32, the Download client.scr button at the bottom of the page needs to be hit. The download is a 22MB, self-extracting RAR file which unpacks into several files totaling over 67MB. The files are then extracted into C:UsersUserAppDataRoamingChromeBrowser, along with a shortcut in StartUp Programs so that the ransomware initiates when the computer boots up.
Some of the extracted files are:
- Chrome – Holds the General Public License agreement.
- chrome.exe – A packaged NW.js file that contains the malware code.
- g – This file stores important information required by the malware. This includes the bitcoin ransom amount, the bitcoin address being used, and an error message if the configuration was enabled to do so.
- rundll32.exe – A TOR executable file that links the malware with the TOR Command and Control server.
- s.exe – This creates the shortcut in the Startup folder.
The malware encrypts the files of the users using Advanced Encryption Standard (AES) and decrypts them only after the asked ransom is paid in bitcoin. Ransom32 specifically targets commonly used file extensions such as .jpg, .jpeg, .tif, .gif, .wma, .avi, .mp4, and .docx. An extensive list of targeted extensions can be found here.
In a blog post titled Meet Ransom32: The first JavaScript ransomware, security expert Fabian Wosar also gave an extensive review of the malware, reiterating that the best protection against the attack remains a solid and proven backup strategy.
Apart from maintaining a backup of important files, users are advised to install the best anti-malware and internet security programs to stay protected from an increasing number of cyber attacks. They might not provide 100% cover but will definitely thwart such malicious attacks with their strong defense.
Image Credits: Bleeping Computers